Congratulations to all the teams who entered and competed in this year’s Network Forensics Puzzle Contest at DEFCON 22. This was our fifth year running the contest, and we saw an incredible turnout of 264 registered teams for one of our most challenging puzzles ever. It was ultimately a test of endurance: teams were required to beat seven progressively more difficult rounds, with the winning team finishing in just over two days.
Congratulations to all the teams who entered and competed in this year’s Network Forensics Puzzle Contest at DEFCON 22. This was our fifth year running the contest, and we saw an incredible turnout of 264 registered teams for one of our most challenging puzzles ever. It was ultimately a test of endurance: teams were required to beat seven progressively more difficult rounds, with the winning team finishing in just over two days.
The eighth bonus round of the contest was attempted by the top three teams but went unsolved at DEFCON. We will ship the prize (an Amazon Fire TV) to whomever can successfully solve the bonus round first! We have a small confession: no one has solved this round yet (including the creators of the puzzle), so we will be impressed to see a solution.
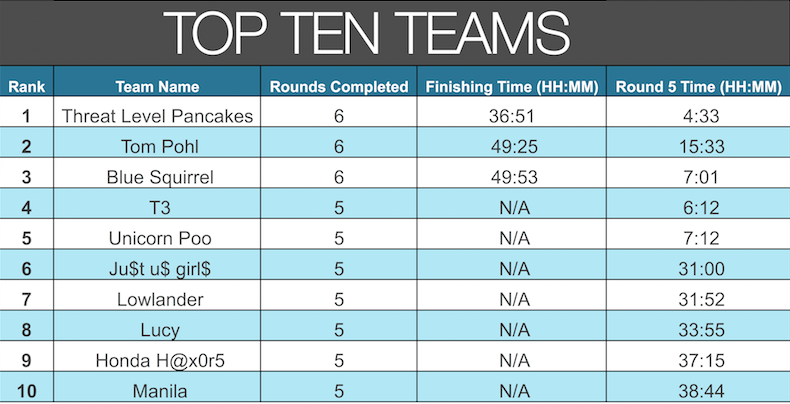
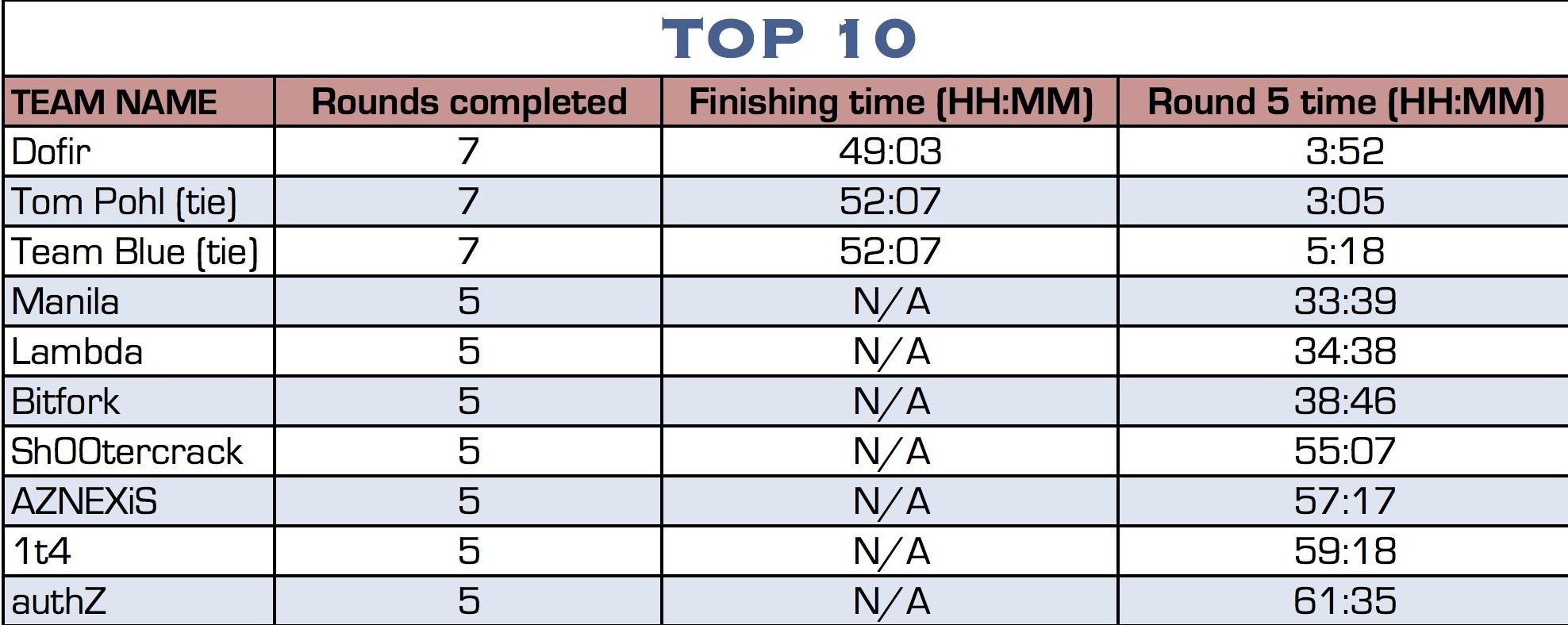
The top 3 finishers:
1st place: Dofir (49 hours, 3 minutes)
2nd place (tie): Tom Pohl and Team Blue (52 hours, 7 minutes)
We hope you grabbed a disc even if you didn’t have time to play along at DEFCON so now you can check out the puzzle on your own. As promised, here are the passwords to unlock the Truecrypt volumes for each round. Please note that zeroes are often used instead of the letter ‘o.’
Round 1: izDEFCONf33ling22?#tSwift
Round 2: #pshth@twaSteh3@$y1#
Round 3: Ib3tuth0ughtQat@r&&
Round 4: h0wd1dug3tth@t1?%
Round 5: ur0nar0lln0w!@
Round 6: gud$luk^^0nth1s1
Round 7: !LA$$t0n3!!
Bonus round: Way-2_1337-4_u!
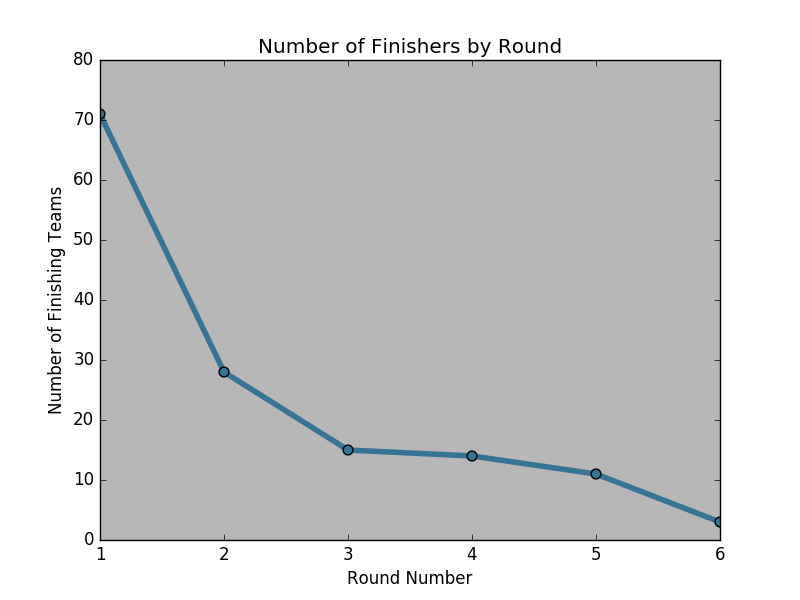
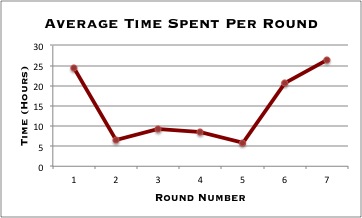
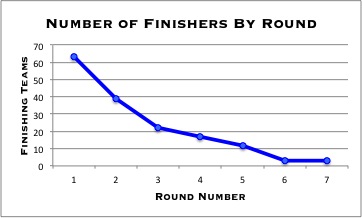
A walkthrough with solutions and the steps to get there will be posted this week. Statistics regarding the progress of participating teams and the time it took to complete each round will also be posted soon.
We would love to hear your feedback about the Network Forensics Puzzle Contest in the comments here or @LMGSecurity on Twitter using the hashtag #NFPC. Thanks for playing!
 If you grabbed a contest disc to play after DEFCON, here are the passwords you’ll need to mount the TrueCrypt volume for each round.
If you grabbed a contest disc to play after DEFCON, here are the passwords you’ll need to mount the TrueCrypt volume for each round.