Finally, it’s what you’ve all been waiting for: the walkthrough and solutions to this year’s puzzle! When you’re ready to see how it’s done, click on the jump to view the walkthrough.
Round 1
Contest password: izDEFCONf33ling22?#tSwift
Question: What is the second name on the list of usernames?
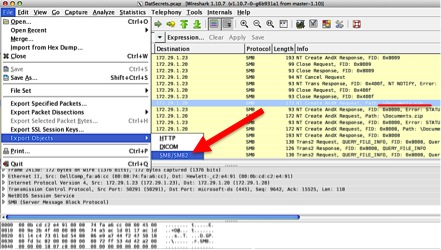
- Export the zip archive “Documents.zip” using Wireshark’s Export Objects utility (under the File tab). Select the SMB/SMB2 option.
- Unzip the contents of the archive and open the file track6.docx in the “Enter the WuTang” directory.
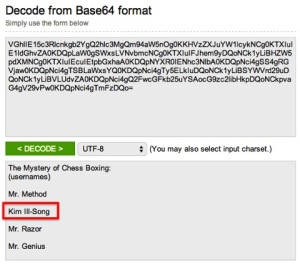
- Decode the base64-encoded text found in the file by using an online decoder or a CLI utility like base64 on Linux. Kim Ill_Song will be the second username on this list.
Answer: Kim Ill_Song
Round 2
Password: #pshth@twaSteh3@$y1#
Question: What city’s official is accepting a non-cash bribe?
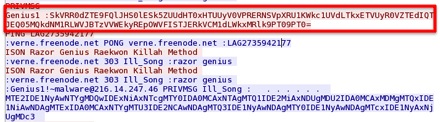
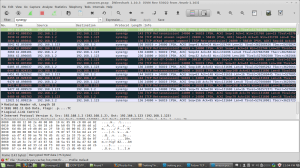
- Filter for IRC traffic using Wireshark’s filtering tool and Follow TCP Stream (under the Analyze tab) for the traffic displayed.
- Within the stream, search for the conversation between Ill_Song and Genius1.
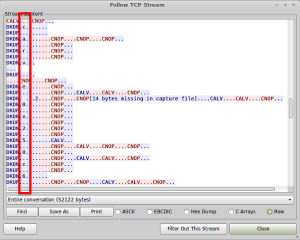
- Copy Ill_Song’s second message sent in this conversation. The message will start with “SkVRR0.”
- Decode this message using a base64 decoder and then decode the output using a base32 decoder. The final output will be a mostly readable sentence with a string of numbers in the middle.
- Copy the string of numbers within the decoded string and paste them into an md5 hash cracker. Once cracked, the output will be “Caracas.”
Answer: Caracas
Round 3
Password: Ib3tuth0ughtQat@r&&
Question: What is the non-cash bribe?
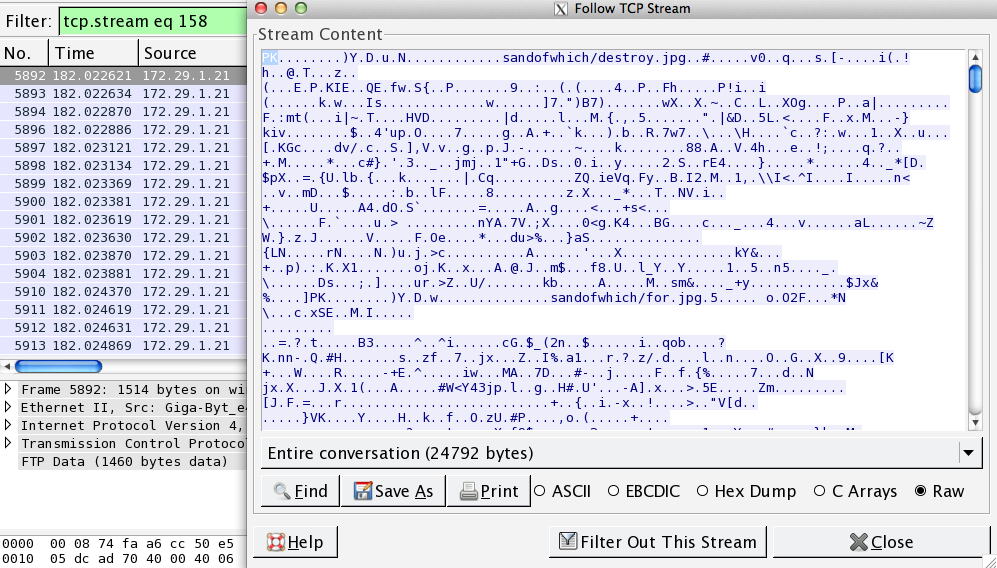
- This round contains five zip archives that need to be carved from the packet capture. Two of these archives (“sandofwhich.zip” and ”ojd34.zip”) can be extracted from the FTP-DATA protocol found in the traffic. Obtaining these archives is as simple as locating the FTP-DATA packets in Wireshark, selecting Follow TCP Stream, and saving the raw contents as a zip archive.
- To carve out the remaining zip archives (“34jdsioj.zip,” ”breaking_bad_season_6.zip,” and ”canc3l.zip”), search for an email correspondence between “kim.illsong” and “da.genius36.” This conversation starts at packet 492.
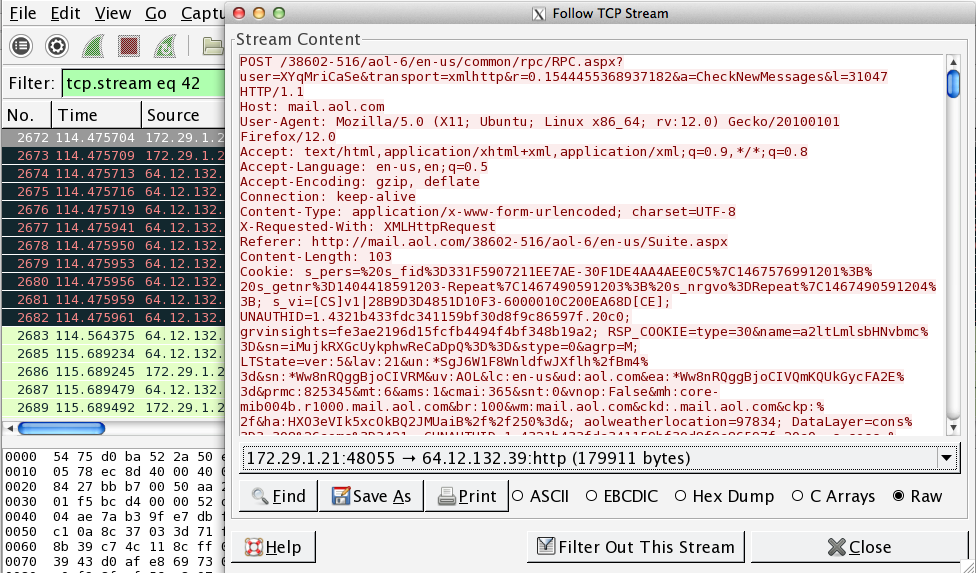
- To carve out the file, open up the TCP stream. Use the dropdown menu toward the bottom of the window to select the side of the conversation being sent from IP address 172.29.1.21 to 64.12.132.39 (the side with red type) and save the raw data.
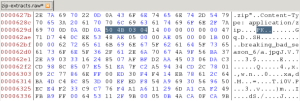
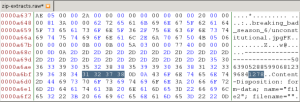
- Open the saved file in your favorite hex editor. (A great Linux hex editor is Bless.) Perform a string search for “filename.” This locates the end of the request header for the first file transfer. Now look for the hexadecimal string “50 4B 03 04.” This is a common “magic number” for zip archives—it marks where carving should begin.
- Search for “filename” again to locate the next archive header. Right above this is the end of the first archive: the long number string “506390528859906812396841278.”
- Copy the text from the magic number stated above to the end of the long number string. Paste this into its own file in your hex editor and save it as a .zip file to extract the first zip archive.
- Repeat this process for the next two zip archives sent via email.
- Once all of the zip archives have been carved out, gather all the JPEG files into one directory.
- The order in which the JPEGs should be reconstructed is determined by this Edward Snowden quote:
I can’t in good conscience allow the U.S. government to destroy privacy, internet freedom and basic liberties for people around the world with this massive surveillance machine they’re secretly building.”
Since there are some duplicate words in the quote, only the first instance of these words is used. The easiest way to reconstruct the correct image is to use the following CLI command:
cat I.jpg cant.jpg in.jpg good.jpg conscience.jpg allow.jpg the.jpg U.S..jpg government.jpg to.jpg destroy.jpg privacy.jpg internet.jpg freedom.jpg and.jpg basic.jpg liberties.jpg for.jpg people.jpg around.jpg world.jpg with.jpg this.jpg massive.jpg surveillance.jpg machine.jpg theyre.jpg secretly.jpg building.jpg > reassembled.jpg
- The reassembled JPEG will be an image of a chess set.
Answer: Chess set
Round 4
Password: h0wd1dug3tth@t1?%
Question: What is the device name of Ill-Song’s computer?
- There is nothing too special about this round—it’s just a little tedious. First, search through the packet capture to find a large grouping of STUN traffic starting at packet 6540.
- Scroll through the traffic until “[email protected]” appears in plain text. This string can be seen in packet 6662, for example.
Answer: drpoppins-735
Round 5
Password: ur0nar0lln0w!@
Question: What is the month, date, and time of their meeting?
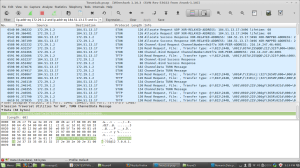
- Two pieces of data need to be found to answer the question. First, the month and time of the meeting are found together in an SMS conversation. Search through the packets to find several POST requests in the HTTP traffic that contain SMS metadata. Some useful search keywords are “Kim Ill-song,” ”SMS,” and “Ann.”
- Search through the SMS conversation until the conversation discussing the meeting date is found in packet 5473. Here we see Kim and Ann are planning to meet in September at 5 PM.
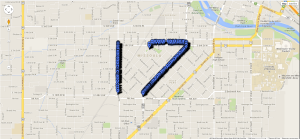
- To find the date of the meeting, we must search for MapQuest GPS coordinates. These coordinates can be viewed in the TCP stream starting at packet 7385.
- In order to see the meeting date, collect and plot enough of these GPS coordinates in Google Maps to see a “17” written on the map.
Answer: September 17th at 5 PM
Round 6
Password: gud$luk^^0nth1s1
Question: What is the Wifi SSID from the device?
- In this round, two pieces of information hidden in previous rounds are required.
- First, we need to find a Python script hidden in round one. Reopen the “Documents” directory found in round 1 and traverse to “More Documents.” This directory contains two files called “BillOfRights.txt” and “NorthKorea.jpeg.” We will need these later.
- The Python script is appended to “NorthKorea.jpeg.” To extract it, rename the picture as a zip file (“NorthKorea.zip”) and use either the command line utility “unzip” or a GUI tool like 7zip on the newly named zip archive. The unzipping process will create an untitled directory containing a script called “broken.py.”
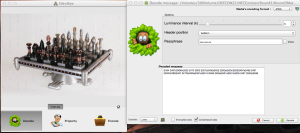
- The second piece of info is steganographically hidden in the image reconstructed in round 3. Obtaining the hidden message in the image requires the steganography tool Silent Eye.
- Open Silent Eye, drag the reconstructed image into the window, and press “Decode.” The passphrase for the decoding is the default password. Press “Decode” again and the following string will appear in the “Decoded message” field:
i2454 2497d2496n2502 2470 2500 2507o2436s2452 2500s2503n2502l2487e2456 2497 2500h2485l2487 2470b2490e2491a2501m2466 2483a2501a2501e2505 2497 2500a2486
-
To utilize the decoded message, “broken.py” must be fixed.
-
You can download the correct code here: cipher.py
- Run the script using the string of characters hidden in the chess set image and the BillOfRights.txt file. The output will be the password “DontTry2BruteForceThisPassword.”
- Now focus on the data found within round six. The files in Egg.zip are an encrypted iOS backup for an iPod touch. To access the SSID stored in the device’s keychain, use this Python script.
- Unfortunately, this script only handles iOS 5 and below. A patch must be applied in order to crack the iOS 7 backup found in round six.
- To decrypt the backup, the following command can be used:
python python_scripts/backup_tool.py c7837a1b219513667089ec628044cfb9f8db2d14/ egg.output
- Enter the password “DontTry2BruteForceThisPassword” to the prompt that is presented after running the script.
- Then, to crack the keychain found in the decrypted backup, use the following:
python python_scripts/keychain_tool.py -d “egg.output/KeychainDomain/keychain-backup.plist” “egg.output/Manifest.plist”
- The script will prompt for a “key835,” but instead enter the hex value of the password “DontTry2BruteForceThisPassword.”
- The output of the final script will be an ASCII table containing the SSID “LeakingSecrets.”
Answer: LeakingSecrets
Round 7
Password: !LA$$t0n3!!
Question: What is the name of the state mentioned in the video?
- Extract the “firetv” directory from the zip archive “TrekkingThruTheAmazon.zip.” Then browse to the directory at /firetv/usr/share/networkFiles/
- This directory contains two PCAP files, “amazon.pcap” and ”trekking.pcap.” Open up “trekking.pcap.”
- We are looking for a zip archive named “jumbled.mp3.zip” that was sent as an AOL email attachment. To extract this archive, follow the TCP stream starting at packet 447 and follow a procedure similar to the one detailed in the round three solution.
- Once the archive is carved out, open the “jumbled.mp3” file contained within. This appears to be a corrupted MP3 file that either stops or skips halfway through depending on your audio software.
- Now open the second PCAP file “amazon.pcap” in Wireshark. This capture contains encrypted wireless traffic. However, with a short search through the capture, we should see that some of the traffic is originating from the wireless network “LeakingSecrets,” to which we found the password (“UncrackableNetwork75”) and SSID in the previous round.
- Wireshark makes decrypting wireless traffic a breeze. For a breakdown of the process, check the Wireshark Wiki.
- After the decryption process is complete, you’ll see traffic with a protocol named “synergy.” Use Wireshark’s “Filter” feature to display only synergy traffic, and follow the TCP stream starting at packet 3817.
- Scroll through the traffic until two strings of characters are displayed vertically in the traffic: carve 0x250c6 and carve 0xa250c5.
- Interestingly enough, these are the hex values to use as offsets to carve “jumbled.mp3.”
- Open “jumbled.mp3” in your favorite hex editor. The two offsets found within the synergy traffic are actually markers for the beginning and end of the Truecrypt volume contained within the MP3 file. To extract the Truecrypt volume, cut out the data above and below these two offsets. However, the data we are about to carve out is important in reconstructing the MP3 file, so open up a second window in your hex editor in which to paste the data above and below the offsets. Make sure to keep the data in its original order.
- Save both the Truecrypt volume and MP3 file.
- Play the MP3 file and the following passcode will be spelled out using the NATO phonetic alphabet: True HOOHA.
- Use this password to decrypt the Truecrypt volume, which will contain a video of Ann Dercover’s confession of her love for Edward Snowden. The state of New Jersey is mentioned in the video.
Answer: New Jersey
Excellent work! You’ve completed the seven main rounds of this year’s contest. If you’re still looking for a challenge, check out the bonus round (password: Way-2_1337-4_u!). An Amazon Fire TV is yours if you are the first person/team to submit a correct answer! Good luck!


Leave a Reply